In ASA you configure a NAT like this (for more detail on that go here):
nat (outside,inside) source static any interface destination static interface Broadcast service WakeOnLan WakeOnLan unidirectional no-proxy-arpUnfortunately this kind of NAT doesn’t work on FTD (version 6.2.1), if you do a packet tracer it seems to work, but it doesn’t.
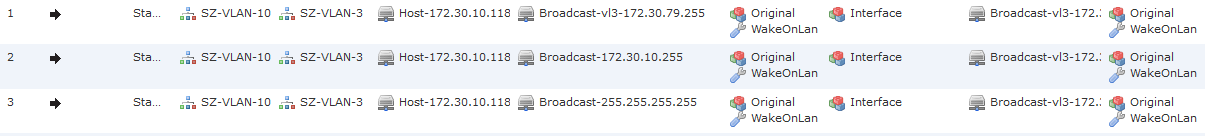
For that example we will use that topology:
srcip: 172.30.10.118/255.255.255.0
srcvlan: 10
dstip: 172.30.79.255/255.255.240.0
dstvlan: 3
dstport: 9019
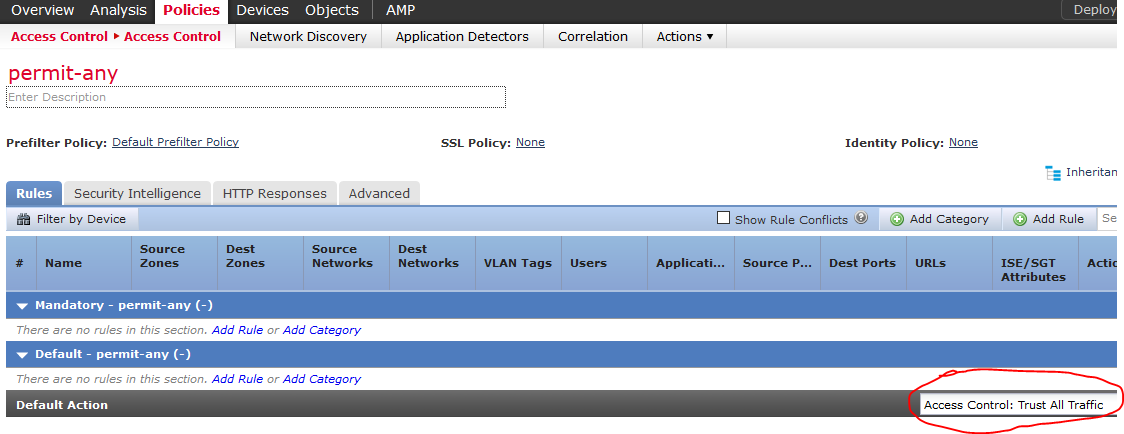
And this policies:
An ACL with a Trust all as default action:
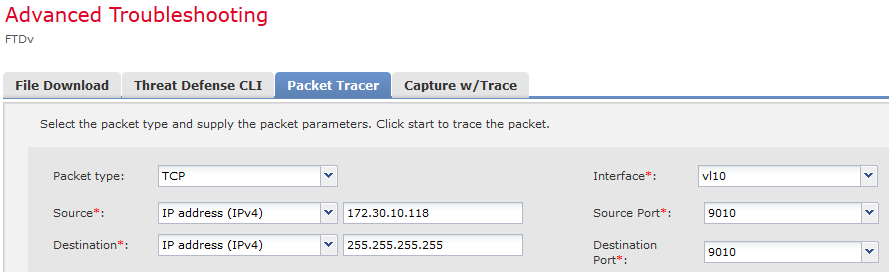
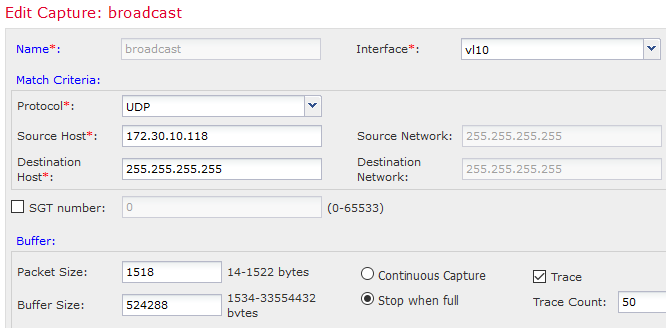
To access packet tracer and capture options open:
 Lets take some outputs form FTD, first let see the packet tracer output to local broadcast address 255.255.255.255:
Lets take some outputs form FTD, first let see the packet tracer output to local broadcast address 255.255.255.255:
Phase: 1
Type: CAPTURE
Subtype:
Result: ALLOW
Config:
Additional Information:
MAC Access list
Phase: 2
Type: ACCESS-LIST
Subtype:
Result: ALLOW
Config:
Implicit Rule
Additional Information:
MAC Access list
Phase: 3
Type: UN-NAT
Subtype: static
Result: ALLOW
Config:
nat (vl10,VL3-OUT) source static Host-172.30.10.118 interface destination static Broadcast-255.255.255.255 Broadcast-vl3-172.30.79.255 service emptyWakeOnLan emptyWakeOnLan unidirectional
Additional Information:
NAT divert to egress interface VL3-OUT
Untranslate 255.255.255.255/9019 to 172.30.79.255/9019
Phase: 4
Type: ACCESS-LIST
Subtype:
Result: DROP
Config:
Implicit Rule
Additional Information:
Result:
input-interface: vl10
input-status: up
input-line-status: up
output-interface: VL3-OUT
output-status: up
output-line-status: up
Action: drop
Drop-reason: (acl-drop) Flow is denied by configured rule
It seems that FTD doesn’t allow broadcasts to pass through it, and a packet capture
1 packet captured
1: 16:32:17.529269 802.1Q vlan#10 P0 172.30.10.118.56125 > 255.255.255.255.9019: udp 102
Phase: 1
Type: CAPTURE
Subtype:
Result: ALLOW
Config:
Additional Information:
MAC Access list
Phase: 2
Type: ACCESS-LIST
Subtype:
Result: ALLOW
Config:
Implicit Rule
Additional Information:
MAC Access list
Phase: 3
Type: UN-NAT
Subtype: static
Result: ALLOW
Config:
Additional Information:
NAT divert to egress interface VL3-OUT
Untranslate 255.255.255.255/9019 to 172.30.79.255/9019
Result:
input-interface: vl10
input-status: up
input-line-status: up
output-interface: VL3-OUT
output-status: up
output-line-status: up
Action: drop
Drop-reason: (sp-security-failed) Slowpath security checks failed
1 packets shown
It seems that it can’t get into the slow path table
Lets see the next example, I’will avoid screenshots from now, so packet tracer from 172.30.10.118 to 172.30.10.255 shows:
Phase: 1
Type: CAPTURE
Subtype:
Result: ALLOW
Config:
Additional Information:
MAC Access list
Phase: 2
Type: ACCESS-LIST
Subtype:
Result: ALLOW
Config:
Implicit Rule
Additional Information:
MAC Access list
Phase: 3
Type: UN-NAT
Subtype: static
Result: ALLOW
Config:
nat (vl10,VL3-OUT) source static Host-172.30.10.118 interface destination static Broadcast-172.30.10.255 Broadcast-vl3-172.30.79.255 service emptyWakeOnLan emptyWakeOnLan unidirectional
Additional Information:
NAT divert to egress interface VL3-OUT
Untranslate 172.30.10.255/9019 to 172.30.79.255/9019
Phase: 4
Type: ACCESS-LIST
Subtype: log
Result: ALLOW
Config:
access-group CSM_FW_ACL_ global
access-list CSM_FW_ACL_ advanced permit ip any any rule-id 268437504 event-log both
access-list CSM_FW_ACL_ remark rule-id 268437504: ACCESS POLICY: permit-any - Default
access-list CSM_FW_ACL_ remark rule-id 268437504: L4 RULE: DEFAULT ACTION RULE
Additional Information:
This packet will be sent to snort for additional processing where a verdict will be reached
Phase: 5
Type: CONN-SETTINGS
Subtype:
Result: ALLOW
Config:
class-map class-default
match any
policy-map global_policy
class class-default
set connection advanced-options UM_STATIC_TCP_MAP
service-policy global_policy global
Additional Information:
Phase: 6
Type: NAT
Subtype:
Result: ALLOW
Config:
nat (vl10,VL3-OUT) source static Host-172.30.10.118 interface destination static Broadcast-172.30.10.255 Broadcast-vl3-172.30.79.255 service emptyWakeOnLan emptyWakeOnLan unidirectional
Additional Information:
Static translate 172.30.10.118/445 to 172.30.64.3/445
Phase: 7
Type: NAT
Subtype: per-session
Result: ALLOW
Config:
Additional Information:
Phase: 8
Type: IP-OPTIONS
Subtype:
Result: ALLOW
Config:
Additional Information:
Phase: 9
Type: NAT
Subtype: rpf-check
Result: ALLOW
Config:
nat (vl10,VL3-OUT) source static Host-172.30.10.118 interface destination static Broadcast-172.30.10.255 Broadcast-vl3-172.30.79.255 service emptyWakeOnLan emptyWakeOnLan unidirectional
Additional Information:
Phase: 10
Type: NAT
Subtype: per-session
Result: ALLOW
Config:
Additional Information:
Phase: 11
Type: IP-OPTIONS
Subtype:
Result: ALLOW
Config:
Additional Information:
Phase: 12
Type: FLOW-CREATION
Subtype:
Result: ALLOW
Config:
Additional Information:
New flow created with id 153, packet dispatched to next module
Phase: 13
Type: EXTERNAL-INSPECT
Subtype:
Result: ALLOW
Config:
Additional Information:
Application: 'SNORT Inspect'
Phase: 14
Type: SNORT
Subtype:
Result: ALLOW
Config:
Additional Information:
Snort Trace:
Packet: UDP
AppID: service unknown (0), application unknown (0)
Firewall: trust/fastpath rule, 'Default Action' , allow
NAP id 1, IPS id 0, Verdict WHITELIST
Snort Verdict: (fast-forward) fast forward this flow
Phase: 15
Type: ROUTE-LOOKUP
Subtype: Resolve Egress Interface
Result: ALLOW
Config:
Additional Information:
found next-hop 172.30.79.255 using egress ifc VL3-OUT
Result:
input-interface: vl10
input-status: up
input-line-status: up
output-interface: VL3-OUT
output-status: up
output-line-status: up
Action: allow
Packet tracer show the packet as allowed, but it doesn’t and a packet cature shows why:
1 packet captured
1: 19:03:04.670833 802.1Q vlan#10 P0 172.30.10.118.49385 > 172.30.10.255.9019: udp 102
Phase: 1
Type: CAPTURE
Subtype:
Result: ALLOW
Config:
Additional Information:
MAC Access list
Phase: 2
Type: ACCESS-LIST
Subtype:
Result: ALLOW
Config:
Implicit Rule
Additional Information:
MAC Access list
Phase: 3
Type: UN-NAT
Subtype: static
Result: ALLOW
Config:
nat (vl10,VL3-OUT) source static Host-172.30.10.118 interface destination static Broadcast-172.30.10.255 Broadcast-vl3-172.30.79.255 service emptyWakeOnLan emptyWakeOnLan unidirectional
Additional Information:
NAT divert to egress interface VL3-OUT
Untranslate 172.30.10.255/9019 to 172.30.79.255/9019
Result:
input-interface: vl10
input-status: up
input-line-status: up
output-interface: VL3-OUT
output-status: up
output-line-status: up
Action: drop
Drop-reason: (sp-security-failed) Slowpath security checks failed
1 packets shown
The last example is to send the packet directly to the egress interface network’s broadcast address, from 172.30.10.118 to 172.30.79.255
Phase: 1
Type: CAPTURE
Subtype:
Result: ALLOW
Config:
Additional Information:
MAC Access list
Phase: 2
Type: ACCESS-LIST
Subtype:
Result: ALLOW
Config:
Implicit Rule
Additional Information:
MAC Access list
Phase: 3
Type: UN-NAT
Subtype: static
Result: ALLOW
Config:
nat (vl10,VL3-OUT) source static Host-172.30.10.118 interface destination static Broadcast-vl3-172.30.79.255 Broadcast-vl3-172.30.79.255 service emptyWakeOnLan emptyWakeOnLan unidirectional
Additional Information:
NAT divert to egress interface VL3-OUT
Untranslate 172.30.79.255/9019 to 172.30.79.255/9019
Phase: 4
Type: ACCESS-LIST
Subtype: log
Result: ALLOW
Config:
access-group CSM_FW_ACL_ global
access-list CSM_FW_ACL_ advanced permit ip any any rule-id 268437504 event-log both
access-list CSM_FW_ACL_ remark rule-id 268437504: ACCESS POLICY: permit-any - Default
access-list CSM_FW_ACL_ remark rule-id 268437504: L4 RULE: DEFAULT ACTION RULE
Additional Information:
This packet will be sent to snort for additional processing where a verdict will be reached
Phase: 5
Type: CONN-SETTINGS
Subtype:
Result: ALLOW
Config:
class-map class-default
match any
policy-map global_policy
class class-default
set connection advanced-options UM_STATIC_TCP_MAP
service-policy global_policy global
Additional Information:
Phase: 6
Type: NAT
Subtype:
Result: ALLOW
Config:
nat (vl10,VL3-OUT) source static Host-172.30.10.118 interface destination static Broadcast-vl3-172.30.79.255 Broadcast-vl3-172.30.79.255 service emptyWakeOnLan emptyWakeOnLan unidirectional
Additional Information:
Static translate 172.30.10.118/445 to 172.30.64.3/445
Phase: 7
Type: NAT
Subtype: per-session
Result: ALLOW
Config:
Additional Information:
Phase: 8
Type: IP-OPTIONS
Subtype:
Result: ALLOW
Config:
Additional Information:
Phase: 9
Type: NAT
Subtype: rpf-check
Result: ALLOW
Config:
nat (vl10,VL3-OUT) source static Host-172.30.10.118 interface destination static Broadcast-vl3-172.30.79.255 Broadcast-vl3-172.30.79.255 service emptyWakeOnLan emptyWakeOnLan unidirectional
Additional Information:
Phase: 10
Type: NAT
Subtype: per-session
Result: ALLOW
Config:
Additional Information:
Phase: 11
Type: IP-OPTIONS
Subtype:
Result: ALLOW
Config:
Additional Information:
Phase: 12
Type: FLOW-CREATION
Subtype:
Result: ALLOW
Config:
Additional Information:
New flow created with id 246, packet dispatched to next module
Phase: 13
Type: EXTERNAL-INSPECT
Subtype:
Result: ALLOW
Config:
Additional Information:
Application: 'SNORT Inspect'
Phase: 14
Type: SNORT
Subtype:
Result: ALLOW
Config:
Additional Information:
Snort Trace:
Packet: UDP
AppID: service unknown (0), application unknown (0)
Firewall: trust/fastpath rule, 'Default Action' , allow
NAP id 1, IPS id 0, Verdict WHITELIST
Snort Verdict: (fast-forward) fast forward this flow
Phase: 15
Type: ROUTE-LOOKUP
Subtype: Resolve Egress Interface
Result: ALLOW
Config:
Additional Information:
found next-hop 172.30.79.255 using egress ifc VL3-OUT
Result:
input-interface: vl10
input-status: up
input-line-status: up
output-interface: VL3-OUT
output-status: up
output-line-status: up
Action: allow
And a packet capture shows the packet going out too:
1 packet captured
1: 22:51:25.969935 802.1Q vlan#10 P0 172.30.10.118.40931 > 172.30.79.255.9019: udp 102
Phase: 1
Type: CAPTURE
Subtype:
Result: ALLOW
Config:
Additional Information:
MAC Access list
Phase: 2
Type: ACCESS-LIST
Subtype:
Result: ALLOW
Config:
Implicit Rule
Additional Information:
MAC Access list
Phase: 3
Type: UN-NAT
Subtype: static
Result: ALLOW
Config:
nat (vl10,VL3-OUT) source static Host-172.30.10.118 interface destination static Broadcast-vl3-172.30.79.255 Broadcast-vl3-172.30.79.255 service emptyWakeOnLan emptyWakeOnLan unidirectional
Additional Information:
NAT divert to egress interface VL3-OUT
Untranslate 172.30.79.255/9019 to 172.30.79.255/9019
Phase: 4
Type: ACCESS-LIST
Subtype: log
Result: ALLOW
Config:
access-group CSM_FW_ACL_ global
access-list CSM_FW_ACL_ advanced permit ip any any rule-id 268437504 event-log both
access-list CSM_FW_ACL_ remark rule-id 268437504: ACCESS POLICY: permit-any - Default
access-list CSM_FW_ACL_ remark rule-id 268437504: L4 RULE: DEFAULT ACTION RULE
Additional Information:
This packet will be sent to snort for additional processing where a verdict will be reached
Phase: 5
Type: CONN-SETTINGS
Subtype:
Result: ALLOW
Config:
class-map class-default
match any
policy-map global_policy
class class-default
set connection advanced-options UM_STATIC_TCP_MAP
service-policy global_policy global
Additional Information:
Phase: 6
Type: NAT
Subtype:
Result: ALLOW
Config:
nat (vl10,VL3-OUT) source static Host-172.30.10.118 interface destination static Broadcast-vl3-172.30.79.255 Broadcast-vl3-172.30.79.255 service emptyWakeOnLan emptyWakeOnLan unidirectional
Additional Information:
Static translate 172.30.10.118/40931 to 172.30.64.3/40931
Phase: 7
Type: NAT
Subtype: per-session
Result: ALLOW
Config:
Additional Information:
Phase: 8
Type: IP-OPTIONS
Subtype:
Result: ALLOW
Config:
Additional Information:
Phase: 9
Type: NAT
Subtype: rpf-check
Result: ALLOW
Config:
nat (vl10,VL3-OUT) source static Host-172.30.10.118 interface destination static Broadcast-vl3-172.30.79.255 Broadcast-vl3-172.30.79.255 service emptyWakeOnLan emptyWakeOnLan unidirectional
Additional Information:
Phase: 10
Type: NAT
Subtype: per-session
Result: ALLOW
Config:
Additional Information:
Phase: 11
Type: IP-OPTIONS
Subtype:
Result: ALLOW
Config:
Additional Information:
Phase: 12
Type: FLOW-CREATION
Subtype:
Result: ALLOW
Config:
Additional Information:
New flow created with id 242, packet dispatched to next module
Phase: 13
Type: EXTERNAL-INSPECT
Subtype:
Result: ALLOW
Config:
Additional Information:
Application: 'SNORT Inspect'
Phase: 14
Type: SNORT
Subtype:
Result: ALLOW
Config:
Additional Information:
Snort Trace:
Packet: UDP
AppID: service unknown (0), application unknown (0)
Firewall: trust/fastpath rule, 'Default Action' , allow
NAP id 1, IPS id 0, Verdict WHITELIST
Snort Verdict: (fast-forward) fast forward this flow
Phase: 15
Type: ROUTE-LOOKUP
Subtype: Resolve Egress Interface
Result: ALLOW
Config:
Additional Information:
found next-hop 172.30.79.255 using egress ifc VL3-OUT
Phase: 16
Type: CAPTURE
Subtype:
Result: ALLOW
Config:
Additional Information:
MAC Access list
Result:
input-interface: VL3-OUT
input-status: up
input-line-status: up
output-interface: VL3-OUT
output-status: up
output-line-status: up
Action: allow
1 packets shown
So it seems that the only way to pass broadcast traffic through an FTD, is configure it to send to the egress net’s broadcast address.